
Check Point uncovers large-scale phishing campaign abusing Facebook’s Business Suite and official domain
With more than 5.4 billion users worldwide (according to Statista), Facebook remains the world’s most influential social platform and a critical marketing channel for small and medium-sized businesses. Its vast reach and trusted brand make it a prime target for attackers, meaning that when a phishing campaign abuses Facebook’s name, the consequences can be especially serious.
Email security researchers at Check Point have recently uncovered a large-scale phishing campaign abusing Facebook’s Business Suite and facebookmail.com features to send convincing fake notifications that appear to come directly from Meta. This method makes their campaigns extremely convincing, bypasses many traditional security filters, and demonstrates how attackers are exploiting trust in well-known platforms.
Over 40,000 phishing emails were distributed to more than 5,000 customers, primarily across the U.S., Europe, Canada, and Australia, targeting industries that rely heavily on Facebook for advertising. These include automotive, education, real estate, hospitality, and finance.
How the Campaign Works
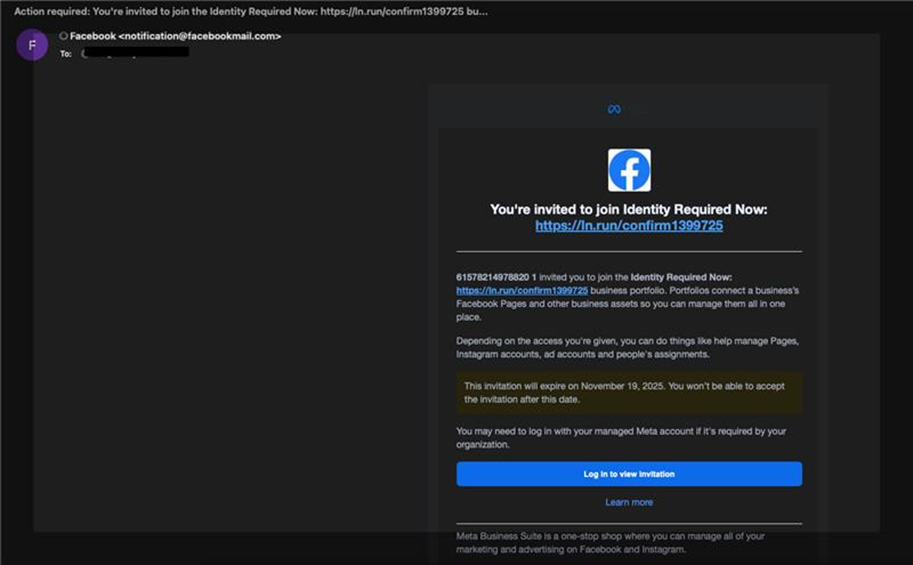
The attack begins with cyber criminals creating fake Facebook Business pages. These pages are modified with logos and names that closely mimic official Facebook branding. Once created, attackers use the Business invitation feature to send phishing emails that appear to be official Facebook alerts.
Crucially, these messages are sent from the legitimate facebookmail.com domain. Most users are trained to distrust strange-looking sender addresses, but in this case, the emails come from a domain they know and trust. As a result, the phishing messages are far more convincing.
What Makes These Emails So Dangerous
The emails were crafted to look identical to genuine Facebook notifications. They used urgent language such as:
- “Action Required: You’re Invited to Join the Free Advertising Credit Program”
- “Meta Agency Partner Invitation”
- “Account Verification Required”
Each email contained a malicious link disguised as an official Facebook notification. Once clicked, victims were redirected to phishing websites, hosted on domains such as vercel.app, designed to steal credentials and other sensitive information.
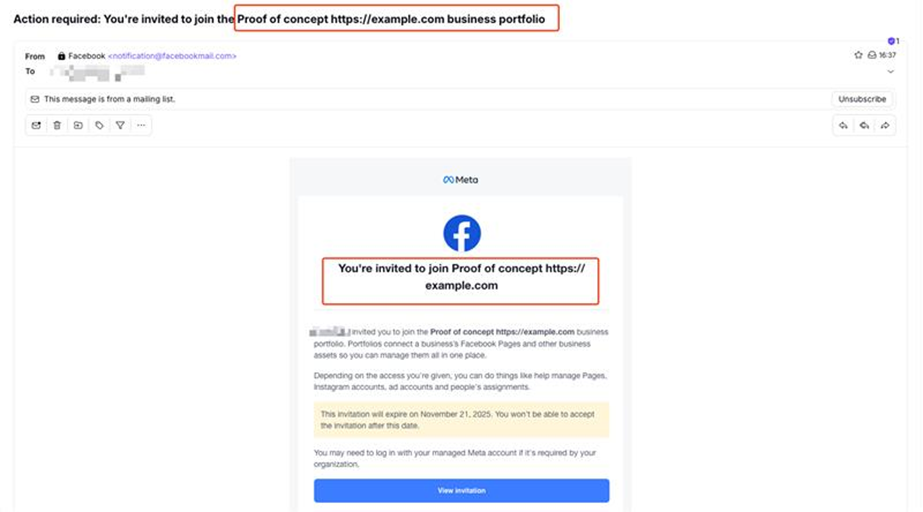
To validate the attack method, our research team performed an internal experiment demonstrating how easily the Facebook Business invitation feature can be abused. We created a fake business page, embedded a message and link in its name, applied a Facebook-style logo, and used the platform’s invitation mechanism to distribute test messages.
Campaign Scale and Patterns
Data from Check Point’s telemetry shows that roughly 40,000 phishing emails were sent across the customer base. While most organizations received fewer than 300 emails, one company alone was bombarded with more than 4,200 messages.
The repetition of nearly identical email subjects and structure suggests a template-driven, mass campaign designed for broad exposure and higher click-through rates, rather than a focused spear-phishing effort.
Who Was Targeted
The campaign primarily focused on small and mid-sized businesses (SMBs) and mid-market enterprises, with a smaller number of large, well-known companies also caught in the mix. These sectors, particularly those that rely on Meta platforms for customer engagement, are ideal targets because their employees frequently receive genuine “Meta Business” notifications and are therefore more likely to trust such messages.
This allowed phishing emails to originate from the authentic facebookmail.com domain — making them extremely convincing and difficult for automated systems to flag as suspicious.
Check Point researchers replicated the technique in a controlled experiment, confirming how easily the Business Invitation feature can be manipulated to send deceptive emails with embedded malicious links.
Why It Matters
This campaign underscores a growing trend where cyber criminals weaponize legitimate services to gain trust and bypass security controls. While the volume of emails may suggest a spray-and-pray approach, the credibility of the sender domain makes these phishing attempts far more dangerous than ordinary spam.
This campaign highlights several important trends in the threat landscape:
- Exploiting trust in major platforms: Attackers are moving beyond spoofed domains and now exploit the built-in features of widely used platforms. By hiding behind Facebook’s legitimate infrastructure, they gain instant credibility.
- Bypassing traditional defenses: Many email security systems rely heavily on domain reputation and sender validation. When malicious messages originate from a trusted domain like facebookmail.com, these defenses often fail.
- Raising questions about platform responsibility: This campaign raises important questions about whether technology giants are doing enough to prevent abuse of their business tools. If attackers can manipulate legitimate features to launch phishing attacks, users and organizations remain at significant risk.
What Organizations Should Do
While it’s critical that platforms like Facebook to address these security gaps, organizations and individuals must also take proactive steps to reduce their risk.
- Educate users: Training should go beyond spotting suspicious domains. Employees and users must learn to question unusual requests, even if they come from trusted sources.
- Implement advanced detection: Security solutions should incorporate behavioral analysis and AI-driven detection that can flag suspicious activity even when messages appear legitimate.
- Enable multi-factor authentication (MFA): Stolen credentials remain the primary goal of phishing campaigns. MFA ensures that even if credentials are compromised, attackers can’t easily gain access.
- Verify the sender and URL. Always check for domain mismatches (e.g., Meta branding with non-Meta links).
- Avoid clicking links in unsolicited emails. Instead, access your Meta Business account directly through the official platform.
How Check Point Protects Customers
Check Point has upgraded SmartPhish to detect and block this specific type of Meta-themed phishing attempt. Continuous monitoring and AI-driven analysis now enable earlier detection of phishing emails that leverage trusted domains.
Looking Ahead
Phishing will continue to evolve, and this campaign demonstrates a worrying trend: attackers are increasingly turning to legitimate services and trusted brands as vehicles for their attacks. As defenders, we must rethink how we identify and block malicious activity, moving beyond traditional filters to a more holistic approach that considers intent, behavior, and context.





